A KMS or Key Management Server is basically a server used to store and generate encryption keys, that can be used by other applications for the purposes of encryption.
We already ran through the process of install HyTrust KeyControl in a VM in a previous post. So in this post, we are going to configure a HyTrust KeyControl KMS to use with a vCenter 6.7.
Lets start by first logging into the Hytrust KeyControl web client - I am logged in with the default root accout "SECROOT" - ofcourse the right way to do this would be use a user account with the required level of permissions, but for this demonstration, the root account is fine.
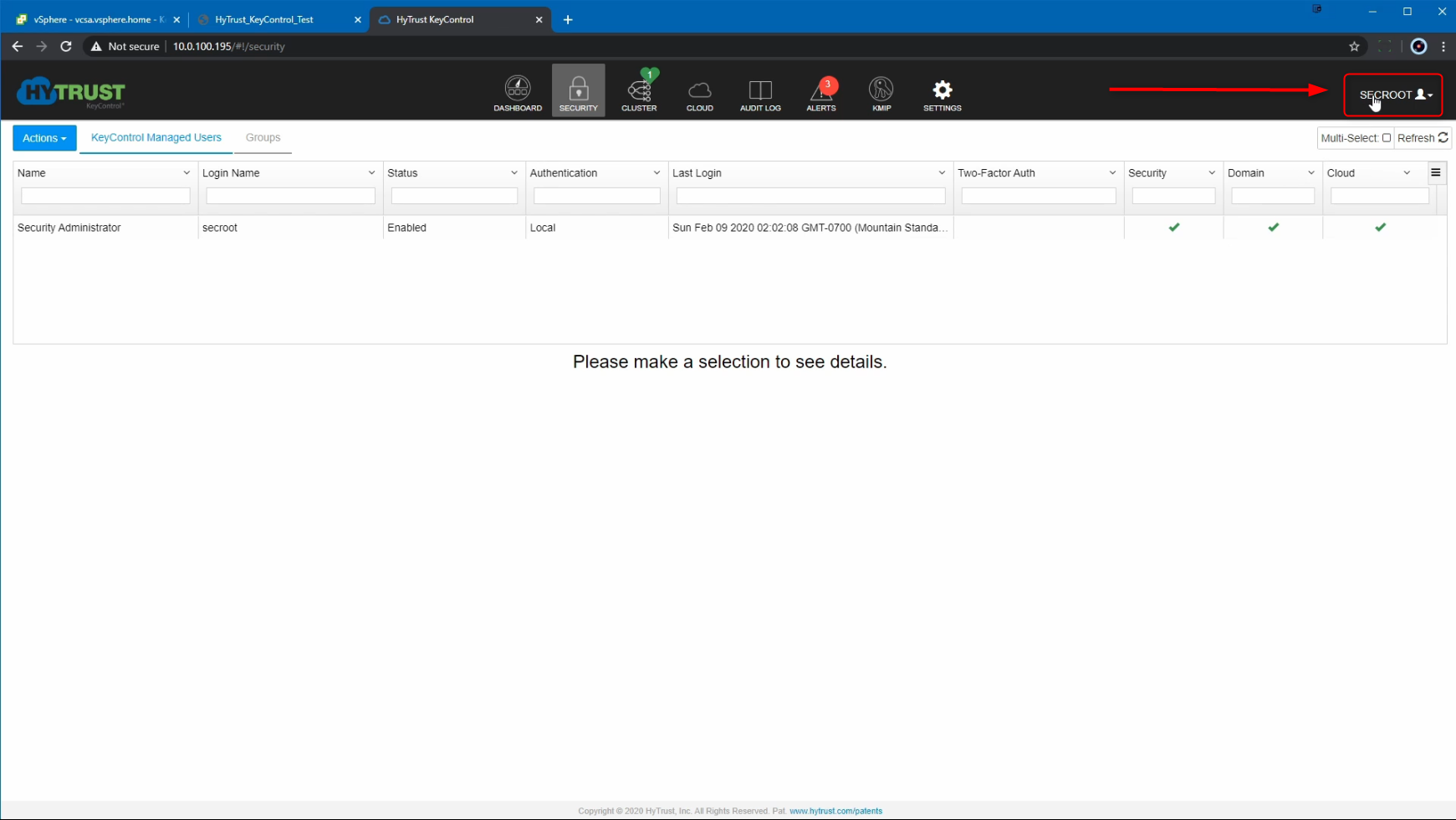
Click on the KMIP Section, and change the "State" of the KMS from DISABLED to ENABLED, click on Apply, and Proceed to overwrite the existing KMIP Server settings.
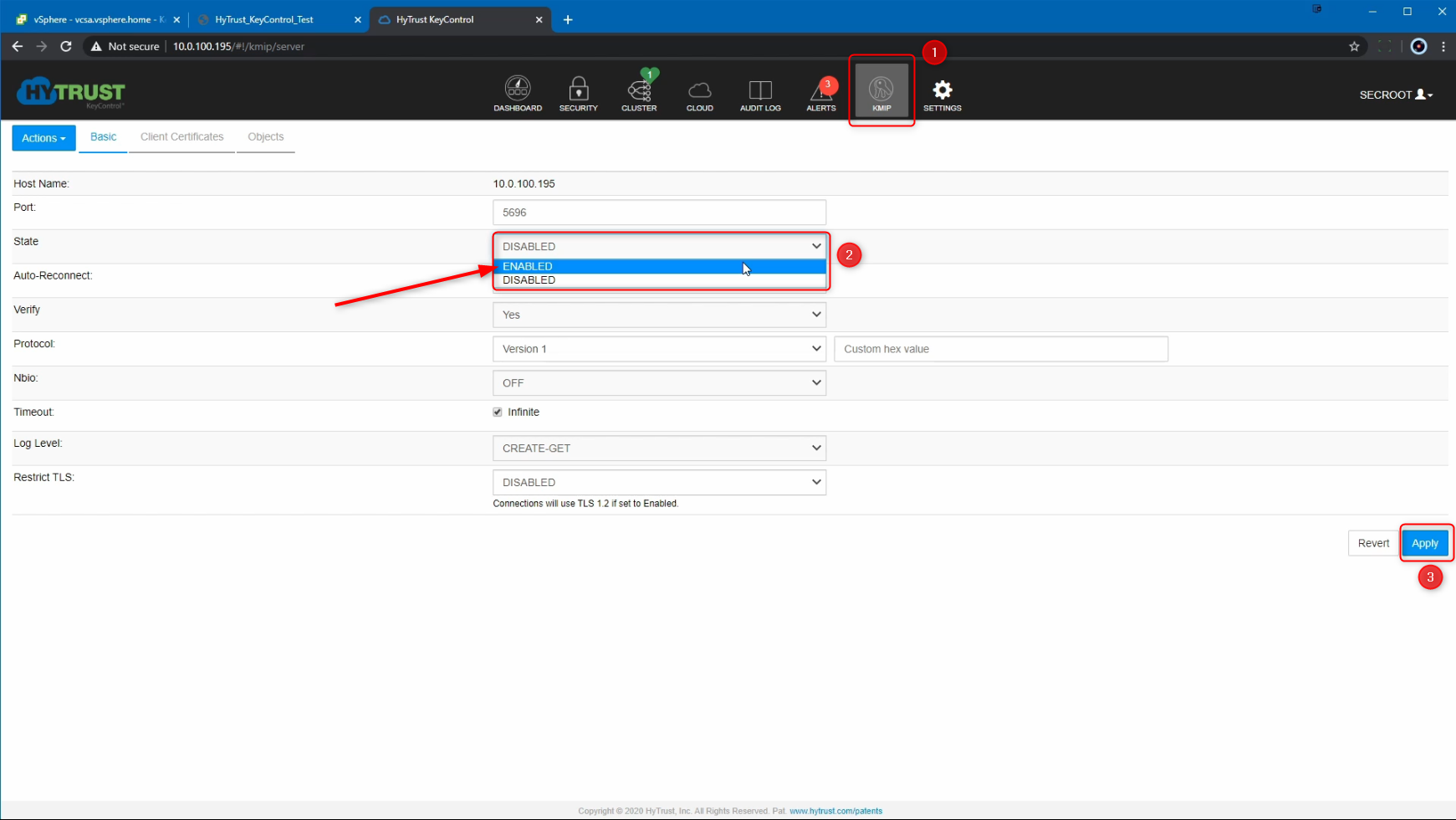
At this point, since we do not have any client certificates, we will need to create a Client Certificate for the KMS Server to trust the vCenter server. Go to Client Certificates > Actions > Create Certificate
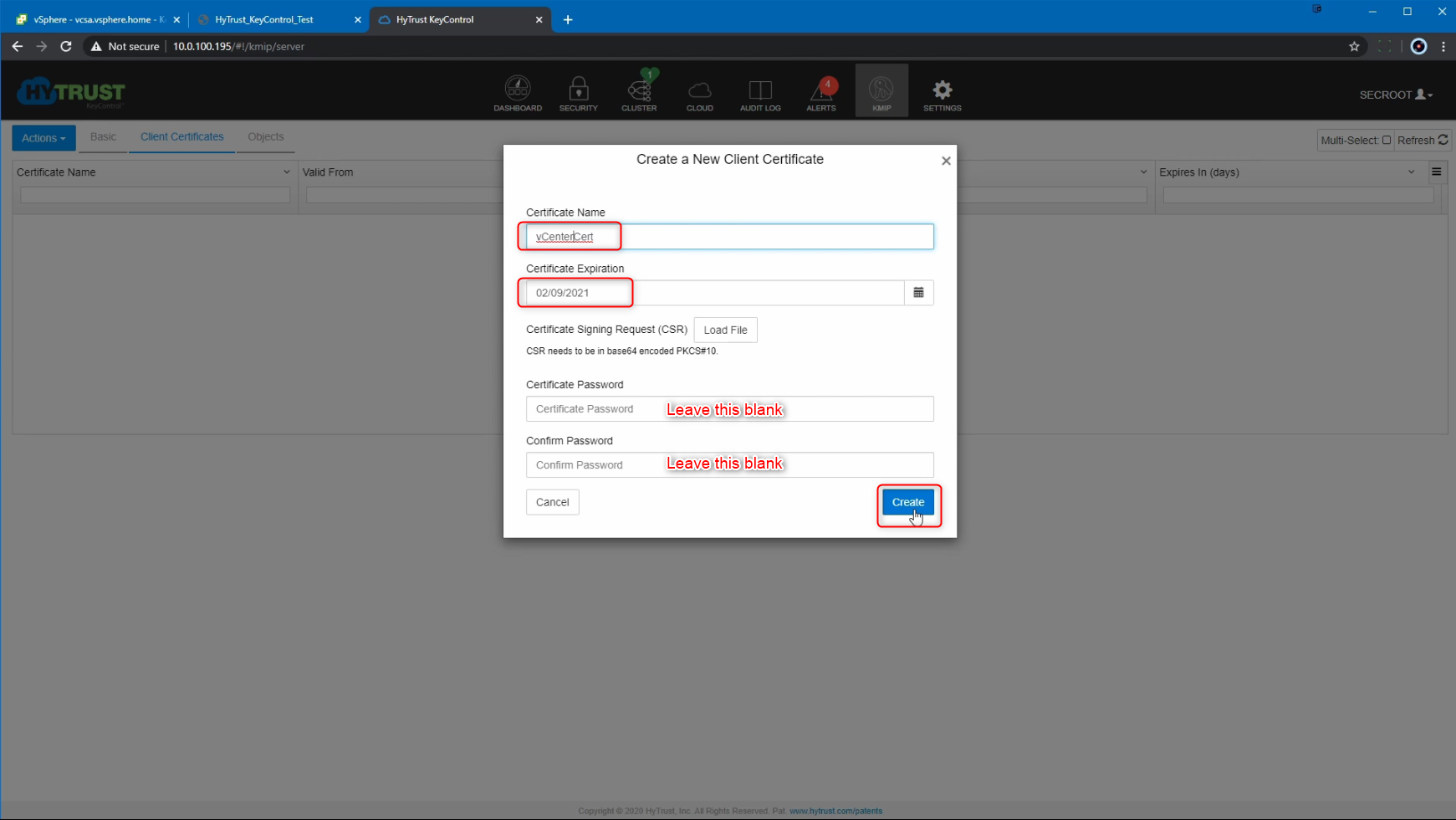
A new dialogue box pops up where we can enter the Certificate name and select the Certificate expiration. We are going to use the name 'vCenterCert'. An important thing to note here is vCenter does not have the ability to decrypt the password for the KMS certificate, or even allow an input for it. So we are going to leave the Certificate Password blank, and then select "Create".
Once the certificate is created, we can select the certificate and then download it locally as a ZIP file. Extracting this ZIP file shows us the CA certificate, and the vCenter leaf certificate. This leaf certificate will be used on the vCenter side.
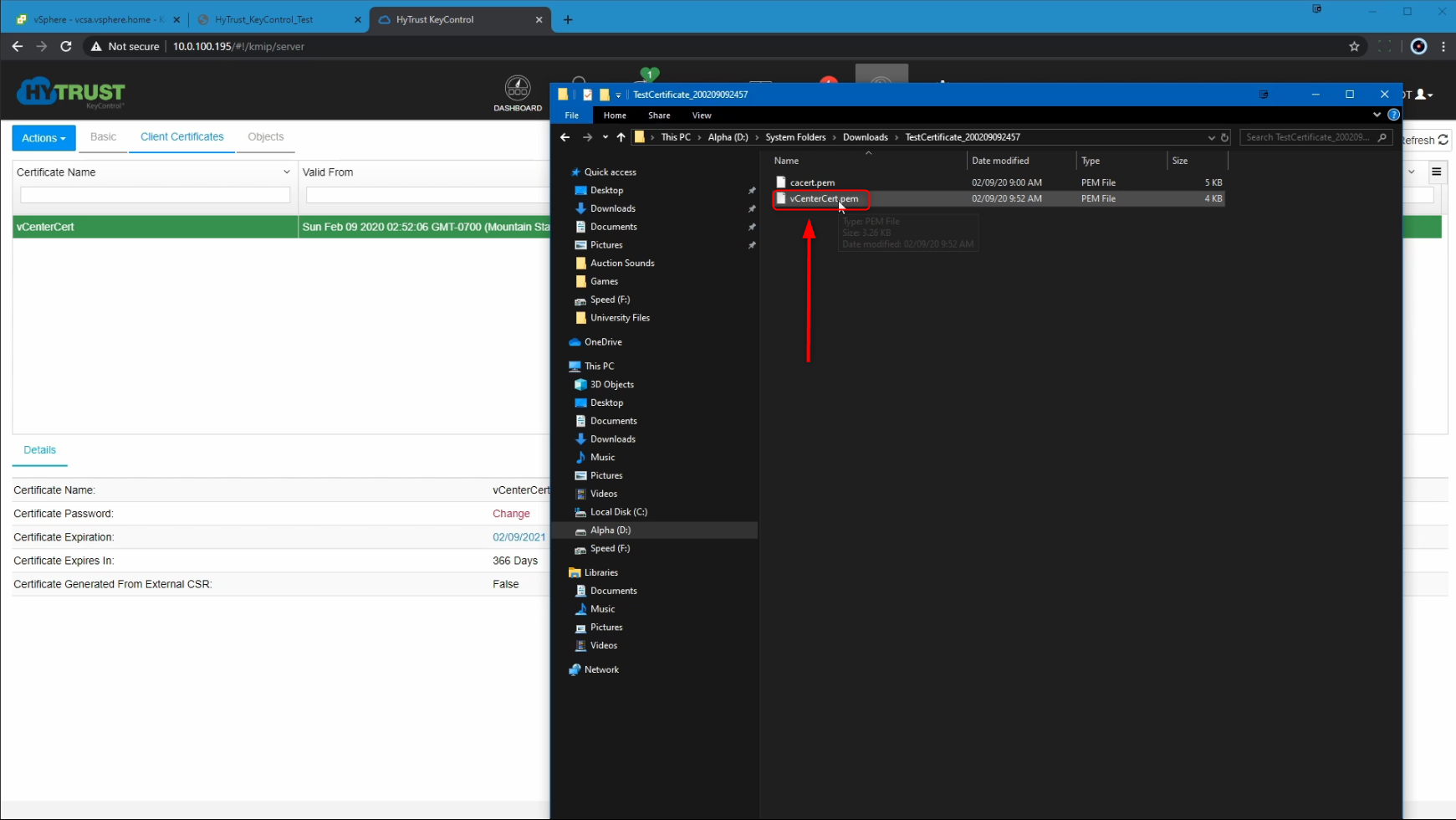
Then we head to the vCenter vSphere Client to complete the configuration on the vCenter side. At the Hosts and Clusters level, we will select the vCenter > Configure > Key Management Servers > Add.
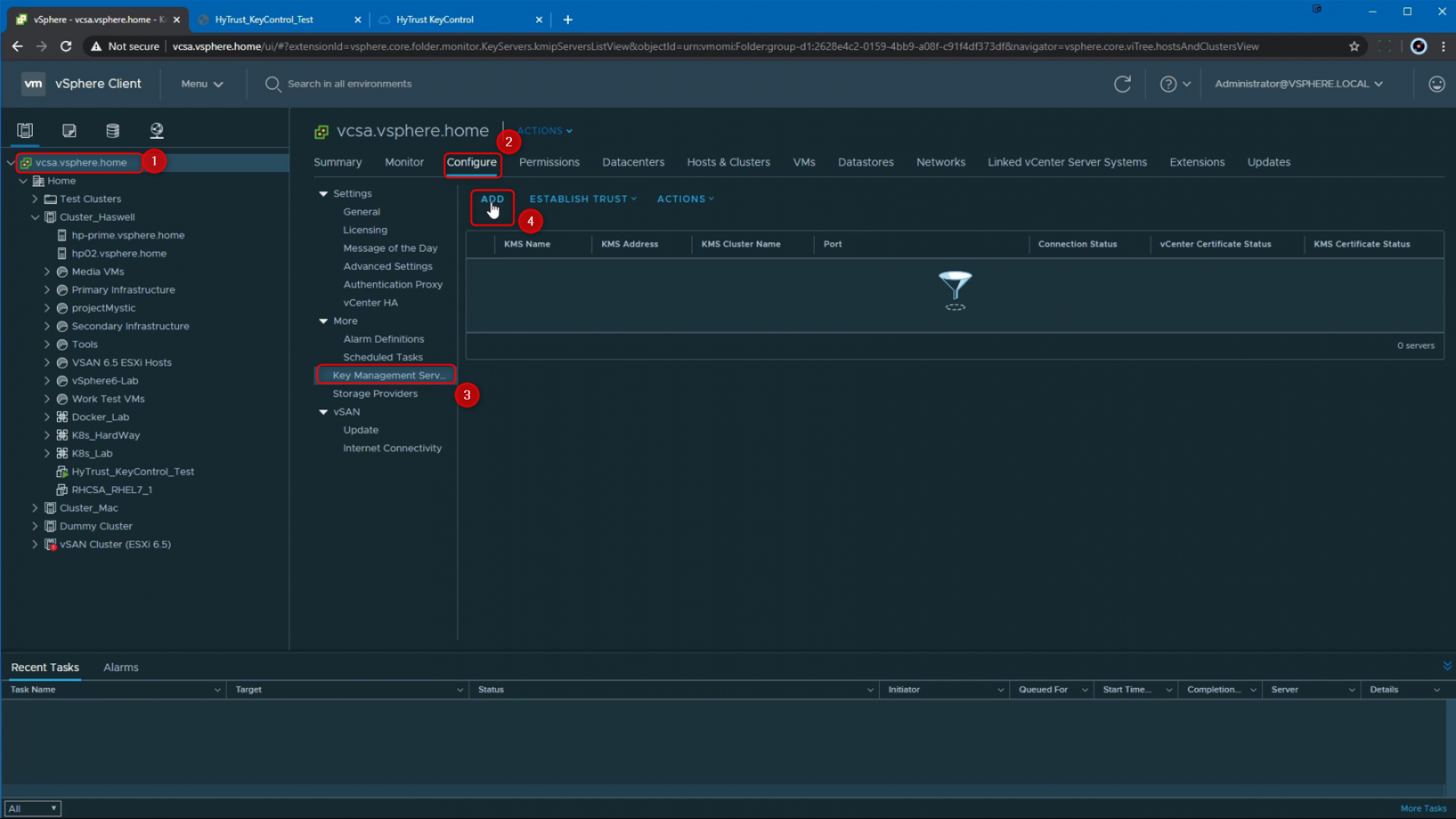
In this dialogue box, we can add a New Cluster Name, which I am going to call "HyTust_Cluster", provide the Server name and IP address of the HyTrust KMS, and provide the Server port - For HyTrust KeyControl, the default port is 5696. We are not using a Proxy, or a specific Username and password, so we are going to leave those fields blank, and finally click on "ADD".
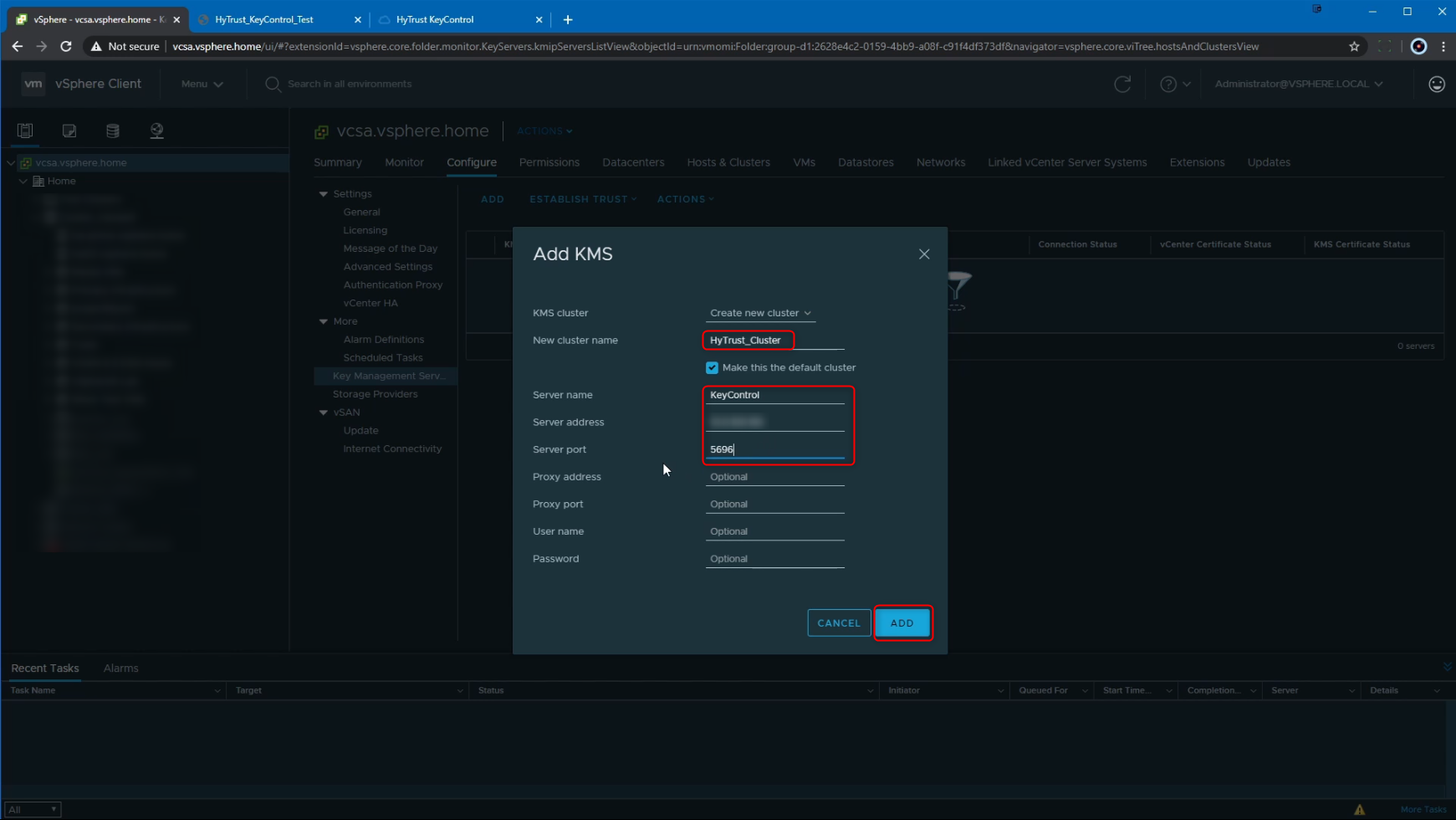
Following that, we see a pop-up with the title "Make vCenter Trust KMS" - Here we can review all the details of the KMS Server Certificate and once we verify that, we can click on "TRUST" to make the vCenter server trust the KMS Server.
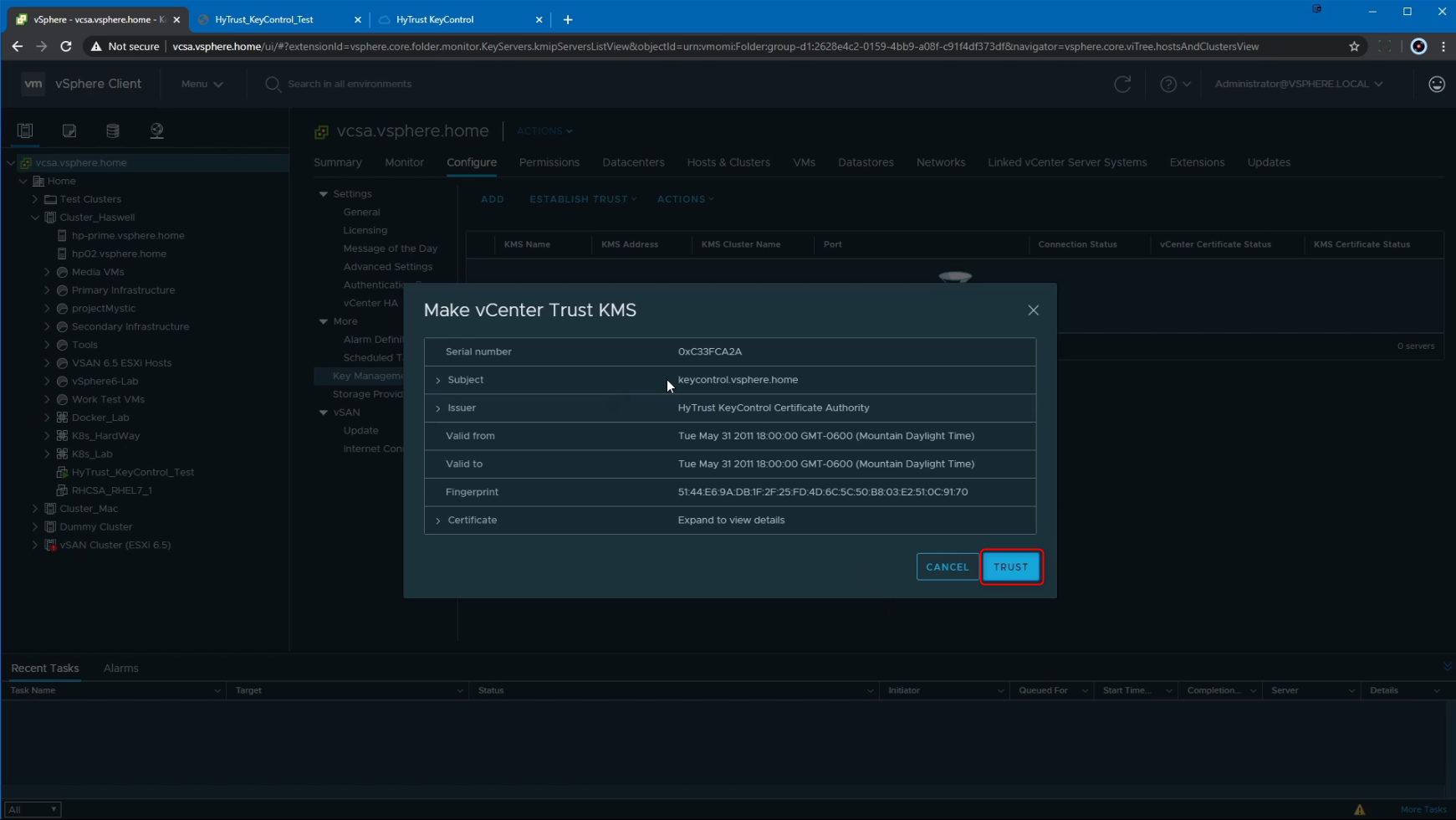
At this point, we see that the KeyControl KMS is added to vCenter, and that vCenter trusts the KMS. The next step is to Make the KMS Trust the vCenter server. So we click on the "Make KMS Trust vCenter" button.
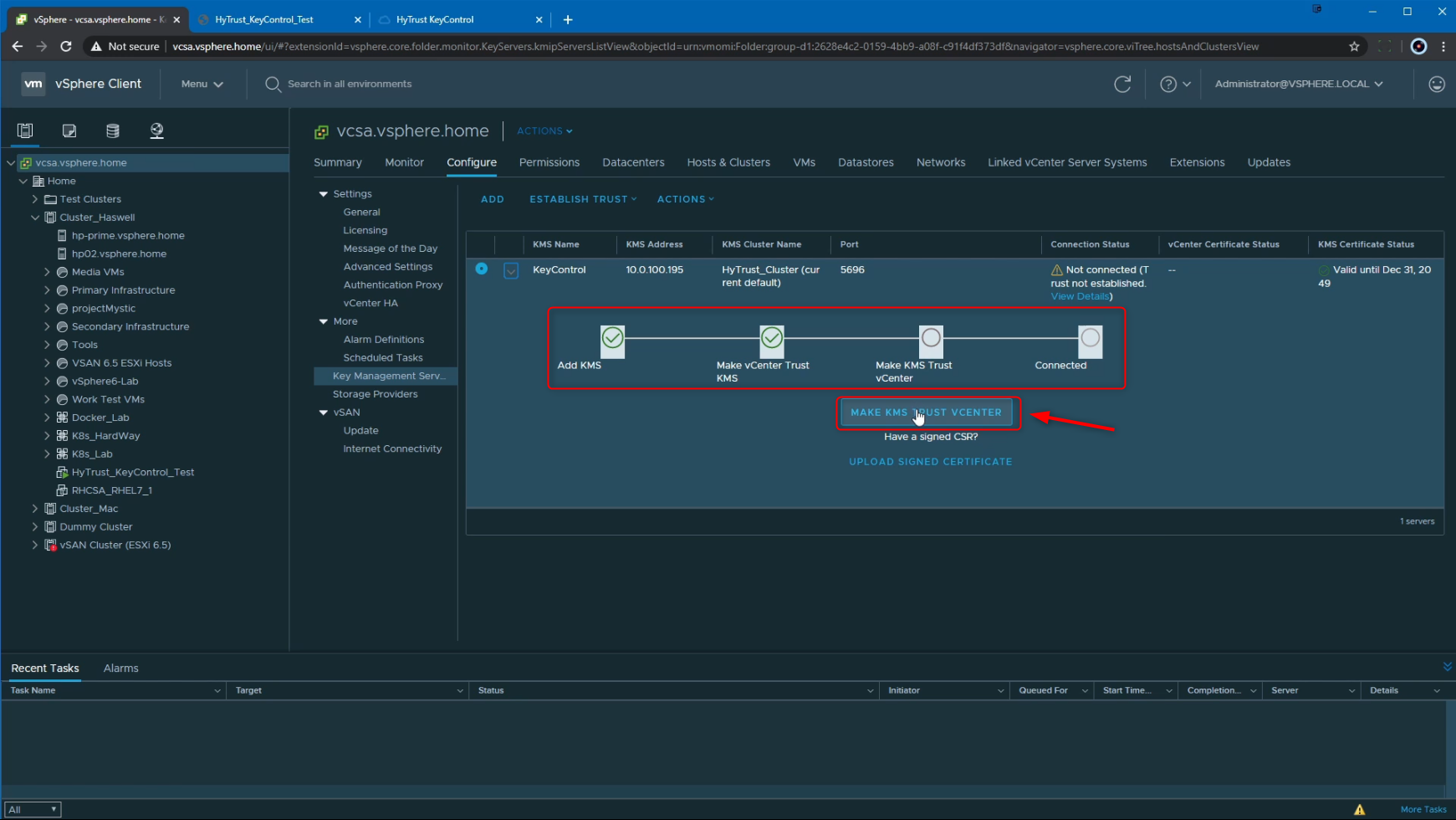
As per HyTrust KeyControl documentation, we have to select option 3 for the trust method and click Next:
KMS certificate and private key
Upload the KMS certificate and private key to vCenter
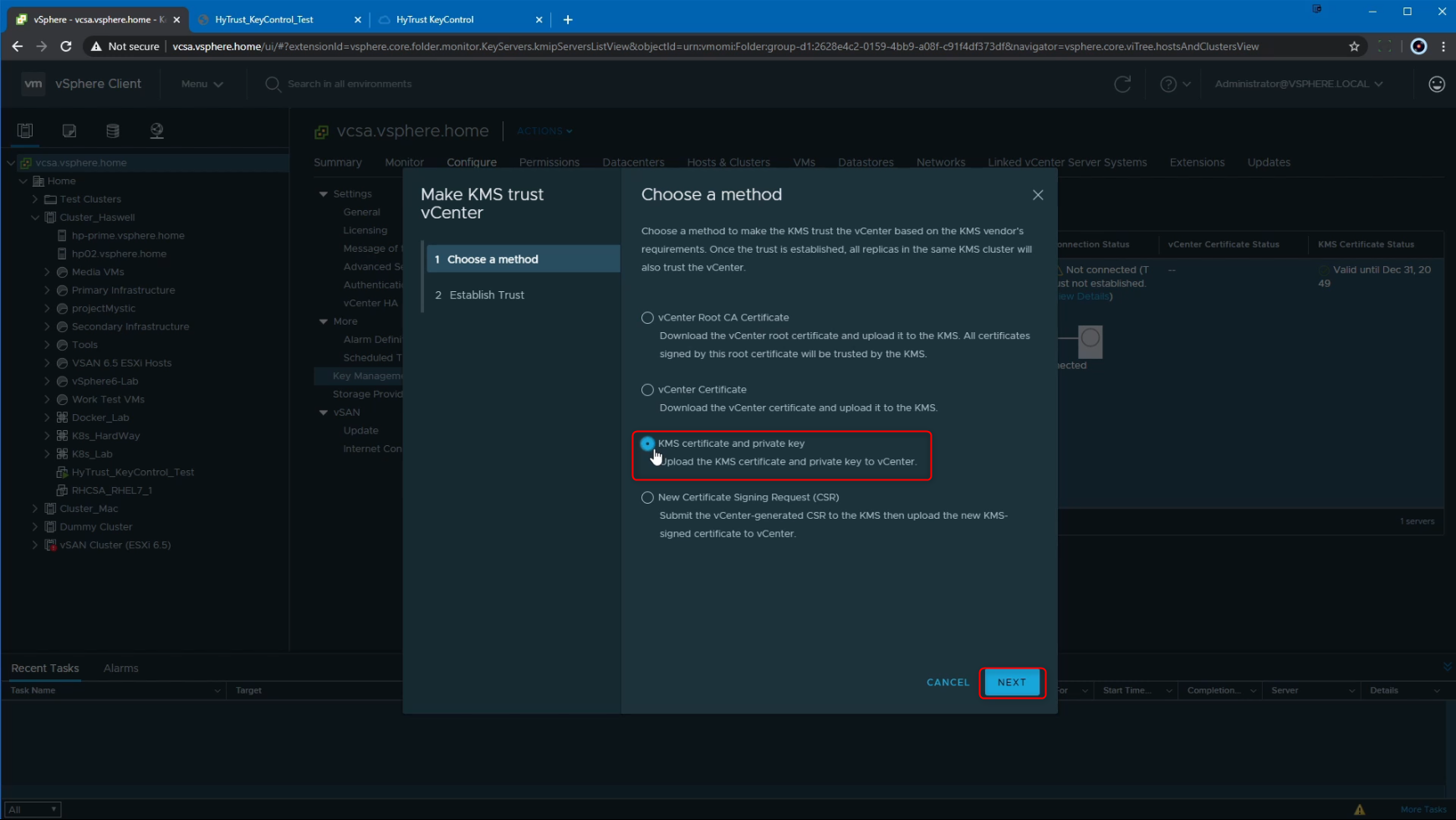
Here we are going to click on "Upload a File" and select the "vCenterCert.pem" certificate that we had downloaded and extracted earlier. Note that we use the same PEM file for both the KMS Certificate and the KMS Private Key, since that PEM certificate has the Certificate and the Private key combined.
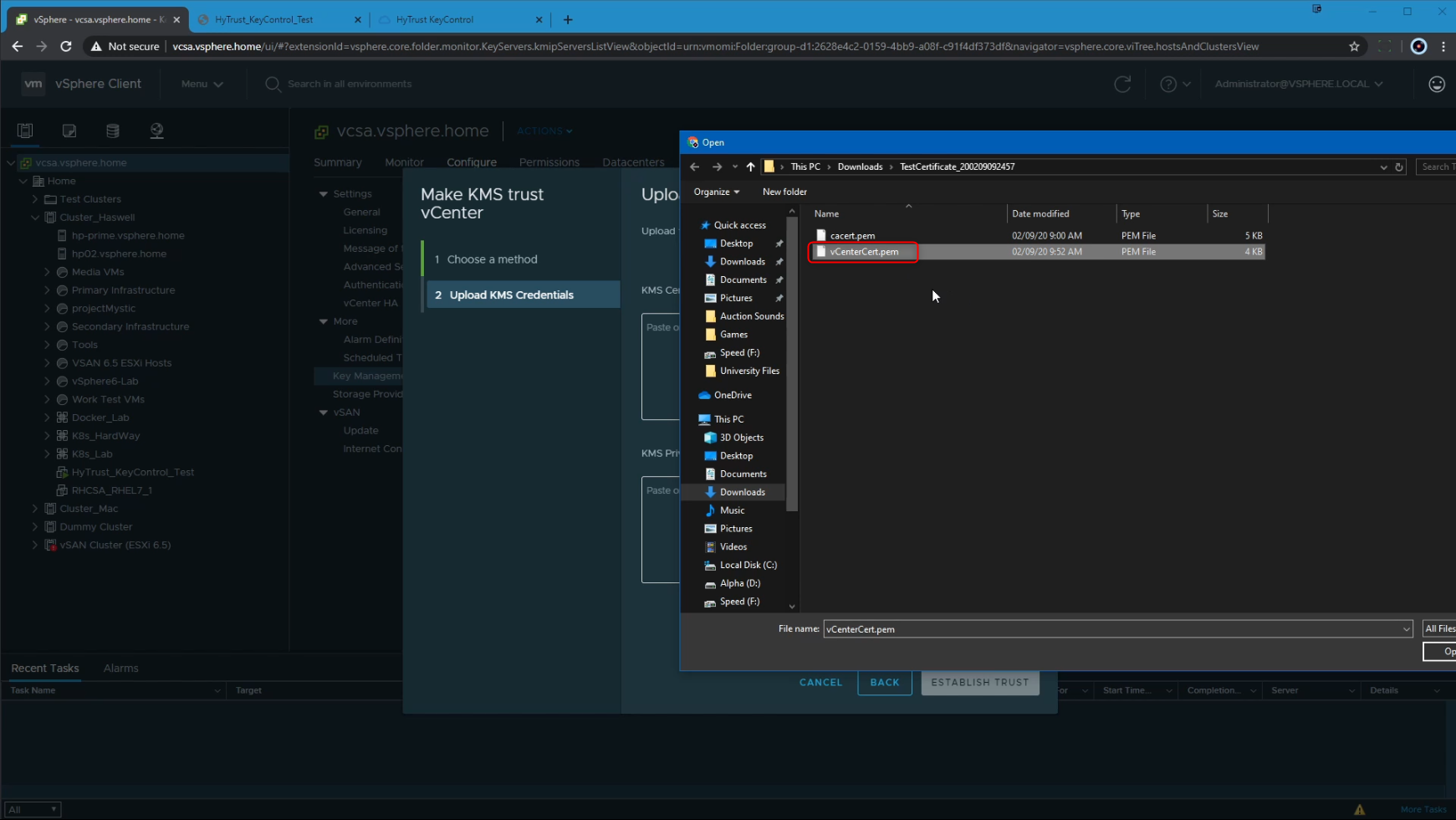
Finally, we click on the Establish Trust button to complete the KMS configuration process for encryption use.
In the next series of posts, we are going to use this KMS to create a VM encryption storage policy, and then use that storage policy to encrypt a VM.
A thing to note here is that the specifics of process of configuring the KMS and how it trusts vCenter, and/or vCenter trusts it depends on the KMS vendor. So, we always need to leverage the vendor documentation for the exact steps on how to configure a particular KMS.
Reference:
https://docs.vmware.com/en/VMware-vSphere/6.7/com.vmware.vsphere.security.doc/GUID-A29066CD-8EF8-4A4E-9FC9-8628E05FC859.html
Update: The process that is described here in this post of configuring a KMS with vCenter in only applicable for versions 6.5 and 6.7
For 7.0, this process changes due to the usage of an Attestation Cluster. I will have a blog post about it when I configure it in my lab.