In our previous posts, we configured a KMS to use with a vCenter, and configured a VM storage policy for encryption.
Here, we are going to encrypt a VM using a VM encryption storage policy.
To start, we need to login to the vCenter vSphere Client and go to the Hosts and Clusters section.
In this example, I am going to encrypt the "RHEL7_1" VM.
To encrypt an existing VM, we are going to have to change its storage policy from its current one, to a VM Storage Policy for Encryption. The VM does need to be powered off for this operation, since we are changing the storage policy affiliated with the VMDKs.
The simplest way to run through this is to Right Click on the VM in question > VM Policies > Edit VM Storage Policies
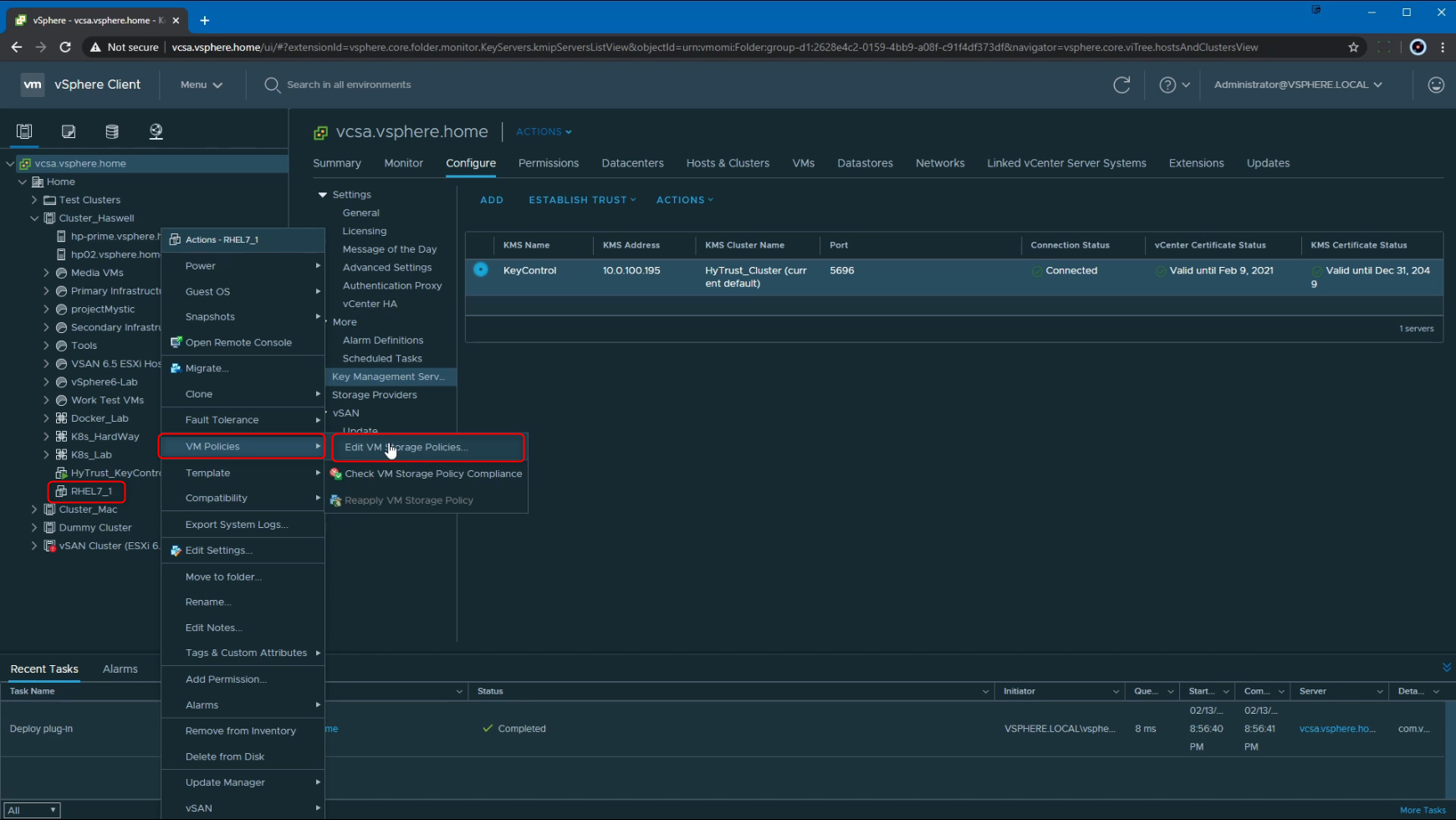
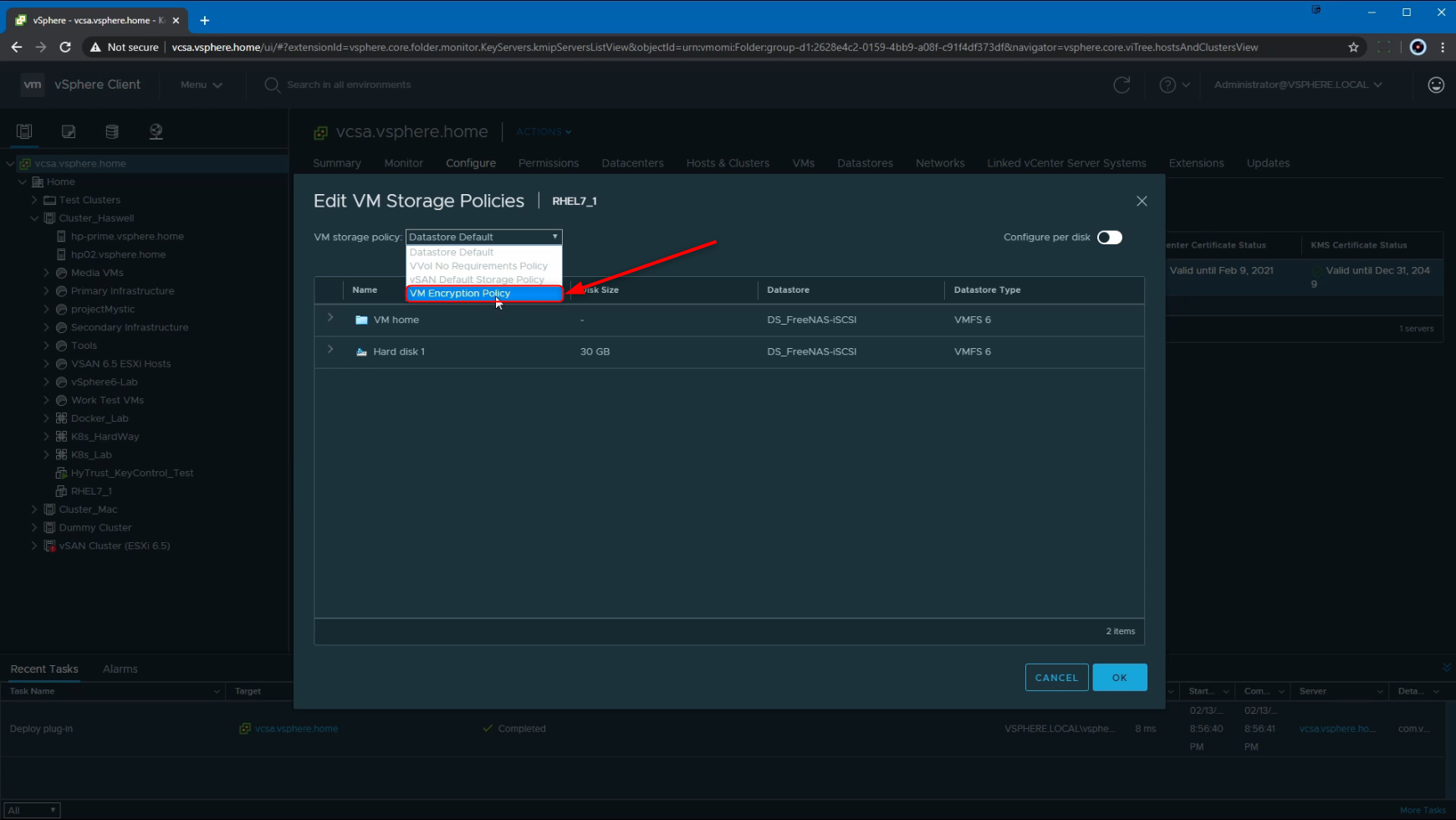
Here, I am selecting the Default VM encryption from the drop down menu. We do also have the option to configure this per disk if needed. In this example, I am going to apply this storage policy to the entire VM, which includes the VMDK as well as the VM configuration files.
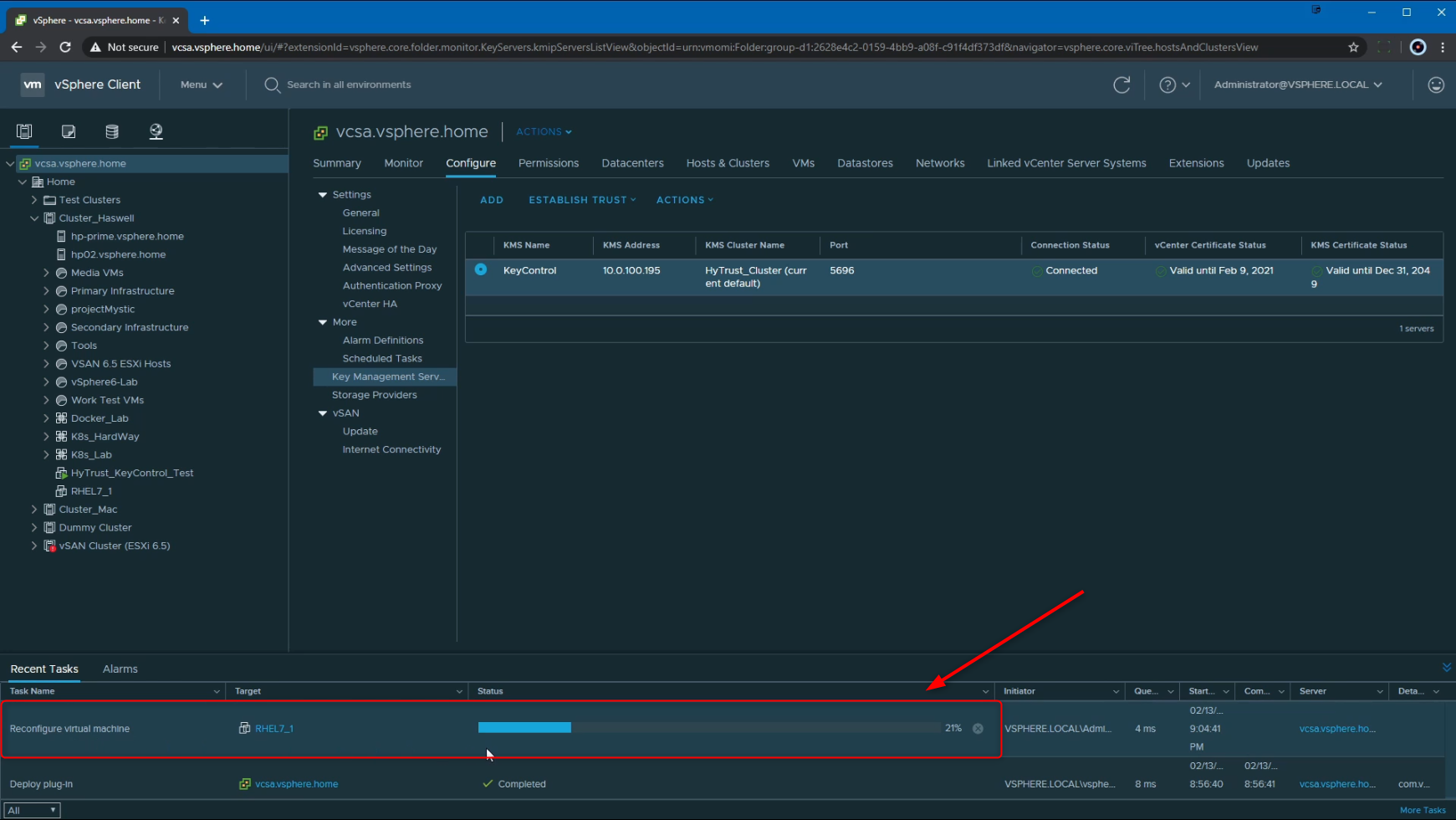
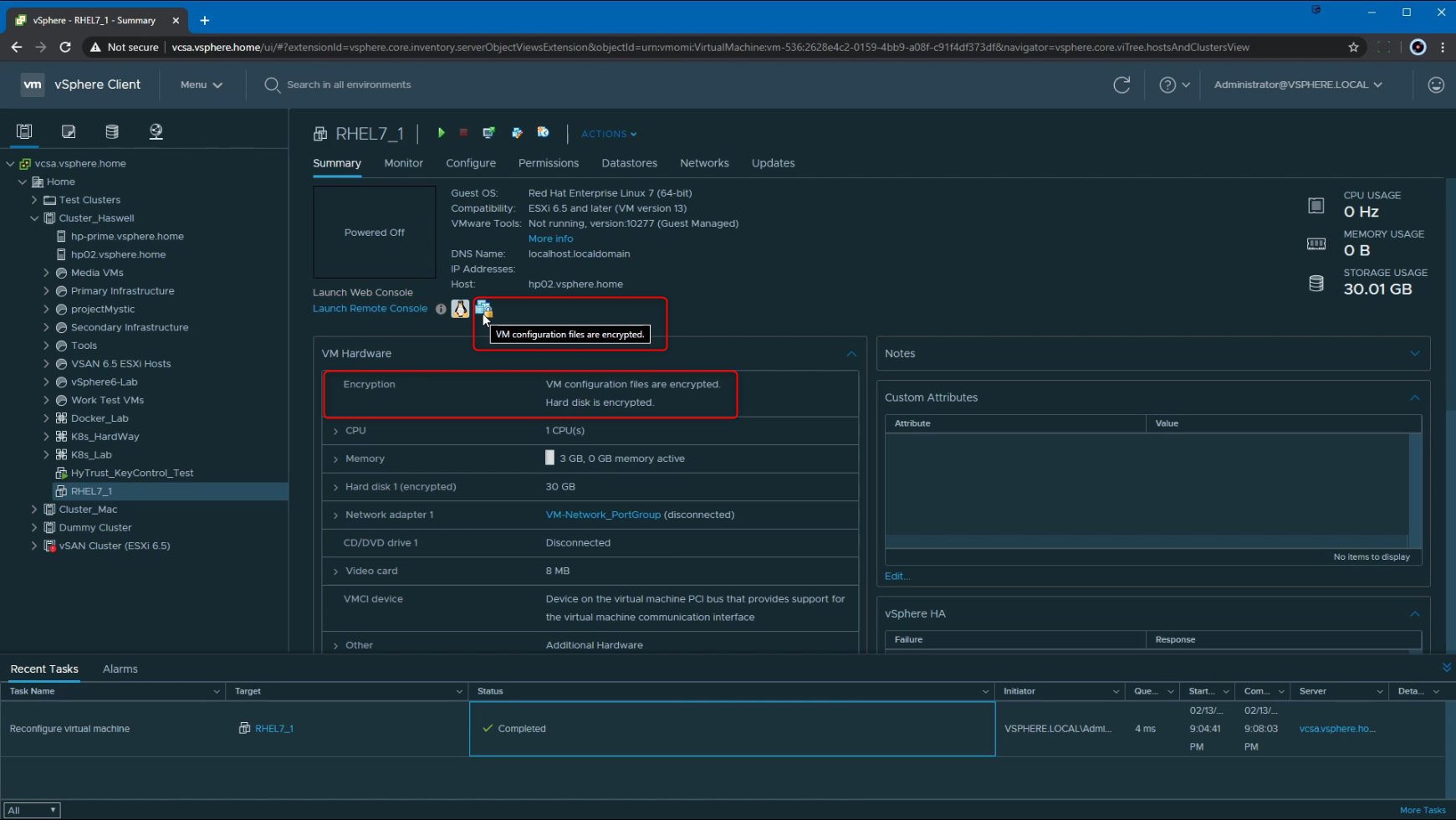
Following that, we see that the Reconfigure virtual machine task is underway. This task can take some time to complete, considering factors like multiple VMDKs associated with the VM, number of VMDKs being encrypted, the size of the VMDK(s) being encrypted etc.
Once the task is complete, we can review the VM to confirm the encryption. Under VM Hardware, we now see that "VM configuration files are encrypted. Hard disk is encrypted". Additionally, there is now a small icon with a lock on it, next to the OS icon which states "VM configuration files are encrypted".
At this point, the VM has been successfully encrypted, and we can power it on to use it. With the VM being encrypted, vSphere vMotion always uses encryption when migrating encrypted virtual machines as well.