Installing HyTrust KeyControl KMS on a VM
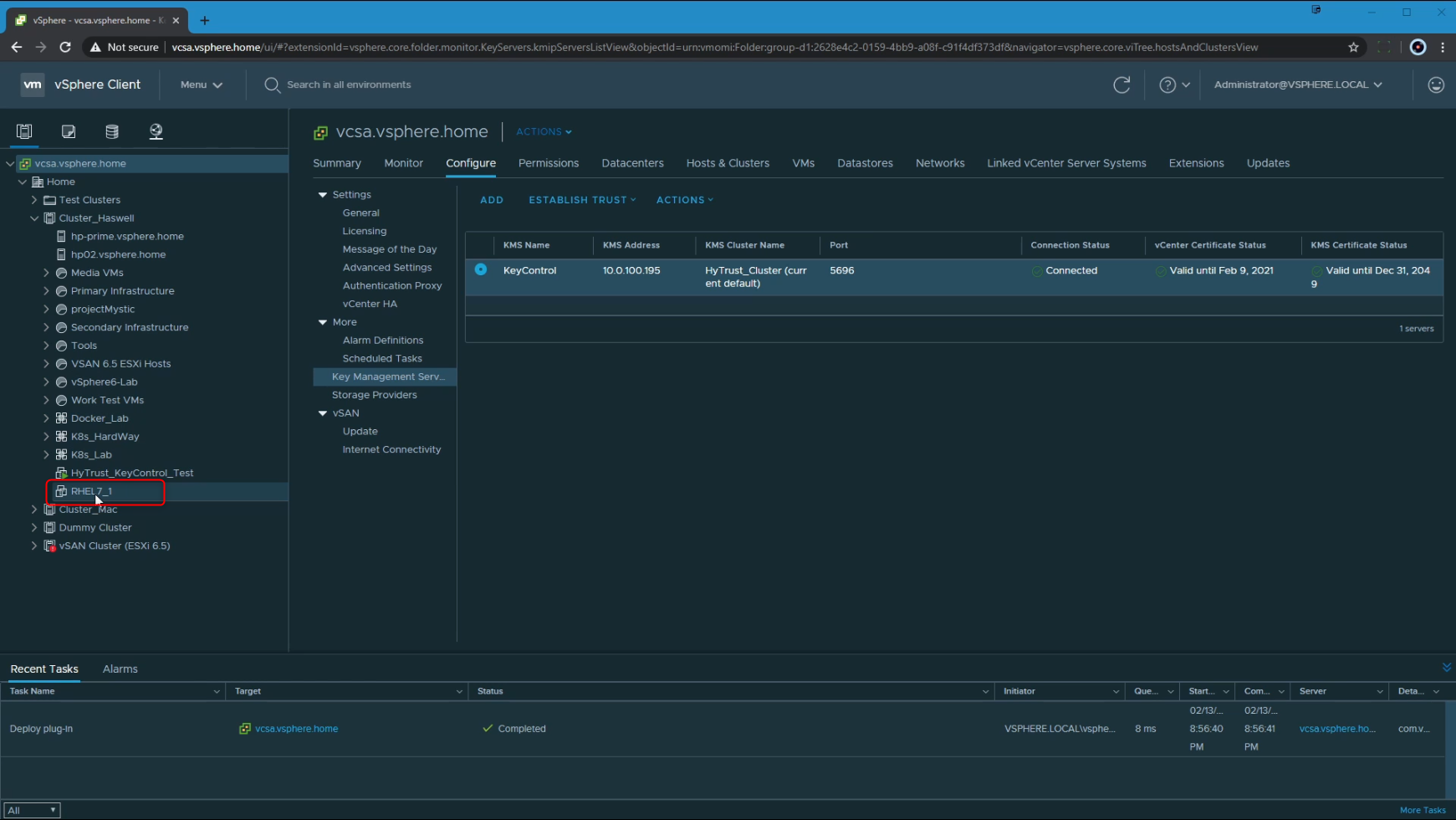
HyTrust (now Entrust) KeyControl is a Key Management Server (KMS) that essentially manages encryption keys for virtual machines, including their rotation, sharing, access etc.
The reason I chose this KMS for use with vCenter is essentially due to the availability of a 60 day trial, which then let me try all the encryption options available within vCenter 6.7
To start off, I downloaded the ISO and uploaded it to a datastore that my ESXi hosts can access. I created a new VM, in this case I called it HyTrust_KeyControl_Test, with the following configuration: